
This article relates to episode 4 in the series ‘Cyber Security in the Ancient World’.
Concealing and hiding information from the enemy, and sending secret messages was among the common practices of ancient intelligence services – starting in the Near East in times of war.[1]
In Herodotus’ Histories we see that Greeks in a Near Eastern context started taking over this practice of sending and hiding secret information (5.28; 7.239; 8.128). We also see the Spartans being linked to this practice for the first time (8.128). In the 2nd century CE, about 700 years after Herodotus lived, we see Plutarch and Aulus Gellius linking the Spartans to one particular method of secret communication: the scytale. According to the authors, the scytale was a method used for sending confidential messages over long distances between the ephorsin Sparta and generals in the field during wars (Plutarch, Life of Lysander, 19.5-7; Aulus Gellius, Attic Nights, 17.9.12-13). However, there is no straightforward evidence that the scytale was used for the purpose of secret messaging. In fact, there is more evidence from the 5thand 4th century BCE that scytalae were used for other purposes, including as a simple staff or baton, a walking stick, a ‘dispatch stick’, and we even find a reference to a phallus.
According to Plutarch, writing in the late 1st/early 2nd-century CE:
When the ephors send out an admiral or a general, they make two round pieces of wood exactly alike in length and thickness, […] and keep one themselves, while they give the other to their envoy. These pieces of wood they call “scytalae.” Whenever […] they wish to send some secret and important message, they make a scroll of parchment long and narrow, like a leathern strap, and wind it round their “scytale” […]. After doing this, they write what they wish on the parchment […]; and when they have written their message, they take the parchment off, and send it, […] to the commander. (Plutarch, Life of Lysander, 19.5-6).
Aulus Gellius’ later 2nd-century CE description is remarkably similar to Plutarch’s:
[When the] ancient Lacedaemonians […] wanted to conceal and disguise […] public dispatches sent to their generals [they] used to send letters written in the following manner. There were two thin, cylindrical wands of the same thickness and length, […]. One of these was given to the general when he went to war, the other the magistrates kept at home […]. [Then] […] they bound about the staff a thong [and] […] they wrote the dispatch on that thong […] When the letter had been written […], the thong was unrolled from the wand and sent to the general, […]. This kind of letter the Lacedaemonians called σκυτάλη [scytale] (Aulus Gellius, Attic Nights, 17.9.6-16).
What Plutarch and Aulus Gellius (following Plutarch) describe is a simple but ingenious device for sending secret messages, whereby only 2 scytalae (literally ‘sticks’) of the same size, and a piece of parchment or papyrus were needed. When a Spartan commander was going to war, the ephors would take two scytalae. They gave one to the commander to take with him and kept the other one in Sparta. The following example shows how this worked according to Plutarch’s and Aulus Gellius’ descriptions, and how the strip of writing material may have looked during the subsequent steps in the process. For this example, the text ‘Enemy attacks at Dawn Tomorrow’ will be used.
1- First, a strip of papyrus or parchment is wrapped about the scytale. In this way small rectangular columns are created. Since the wrapping was done by hand, it is likely that the edges of the strip overlapped each other. Therefore, the columns were not all the same in size.

Erasmus in his early 16th-century work Adages, believed that both the stick and a leather thong wrapped around the stick together were called a scytale (Desiderius Erasmus, Adages, Edition Mynors Volume 33, 1991, p.78; Volume 34, 1992, p.50). Erasmus here, potentially confused Plutarch’s and Aulus Gellius’ descriptions of the scytale since while Aulus Gellius mentioned that the letter that was sent to the general was called a scytale(Aulus Gellius, Attic Nights, 17.9.6-16), while Plutarch suggested that either the stick or the leather strap were both called scytale (Plutarch, Life of Lysander, 19.7).
Cardano in his 1550 work De Subtilitate – simply mentioned cylinders (scytalae) that were used for secret communication by the Spartans without giving any details on how this worked and what materials were used for it. This may indicate that Cardano knew about Plutarch’s and Aulus Gellius’ descriptions but found it unnecessary to repeat them in his own work (De Subtilitate, 17.1036). Perrin translates the word βιβλίον (biblion) as ‘parchment’ in the Loeb version of Plutarch’s Life of Lysander as Poe already did in his 1841 work A Few Words on Secret Writing.[2] And Smith, Kahn and Mollin seem certain that parchment was used instead of papyrus.[3]
However, both papyrus and leather parchment were typically used as writing materials in antiquity, so there seems to be no particular significance attaching to the use of either as the medium for the scytale’s encrypted messages. It seems plausible that leather parchment would offer a more robust material for messages that might need to be sent over long distances, over difficult terrain, and in conflict situations: a context in which the scytale was used (Plutarch, Life of Lysander, 19.5; Aulus Gellius, Attic Nights, 17.6).[4] Yet, while on campaign one obviously had to be able to write and send messages simply and quickly, so where papyrus was readily to hand this would presumably have offered a convenient alternative medium.
2- In the second step, the text was written on the strip of writing material. In Figures 2 and 3 (below), the text is written from left to right and top to bottom on two lines.
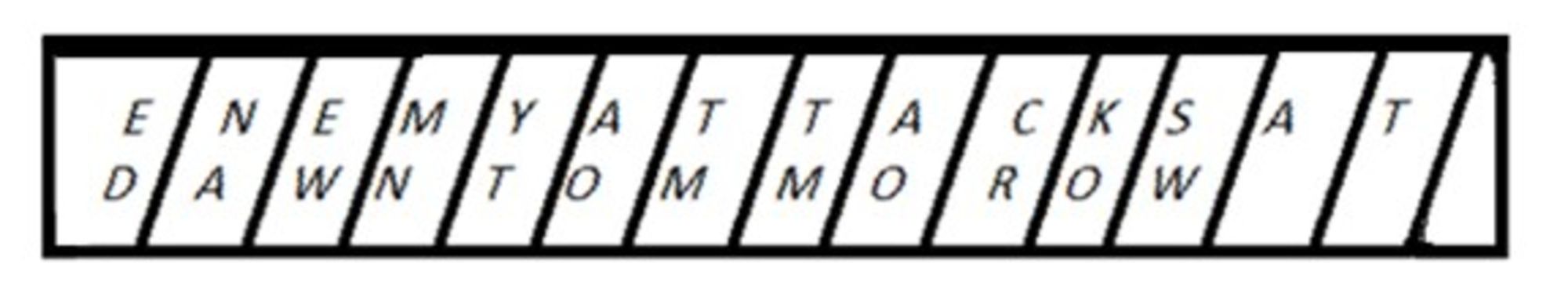
3- As Plutarch describes in his account of the scytale, once the strip of writing material had been unwrapped from the scytale, all letters would have been rearranged and the recipient could not get any meaning out of it since the letters had no connection (Life of Lysander, 19.7). By unwrapping the strip, the letters would now appear per column, instead of per row. So, instead of reading E-N-E-M-Y, the first word of the message, one would now read E-D-N-A-E et cetera (see Figure 3). In Figure 3, every letter of the message has been written on a complete piece of material strip. In other words, no letters were written over the edges of the strip, meaning that when the strip was subsequently removed from the scytale stick, all the letters would have remained intact and would simply have been rearranged in their order of sequence.

4- However, according to Plutarch, the complete scytale was covered in the writing material (Plutarch, Life of Lysander, 19.6). This makes it more plausible that the sender of a message did not in practice write with all letters neatly contained upon complete pieces of the scytale’s material strip, but that the letters of the message would also have been written across the edges of the strip (Figure 4).
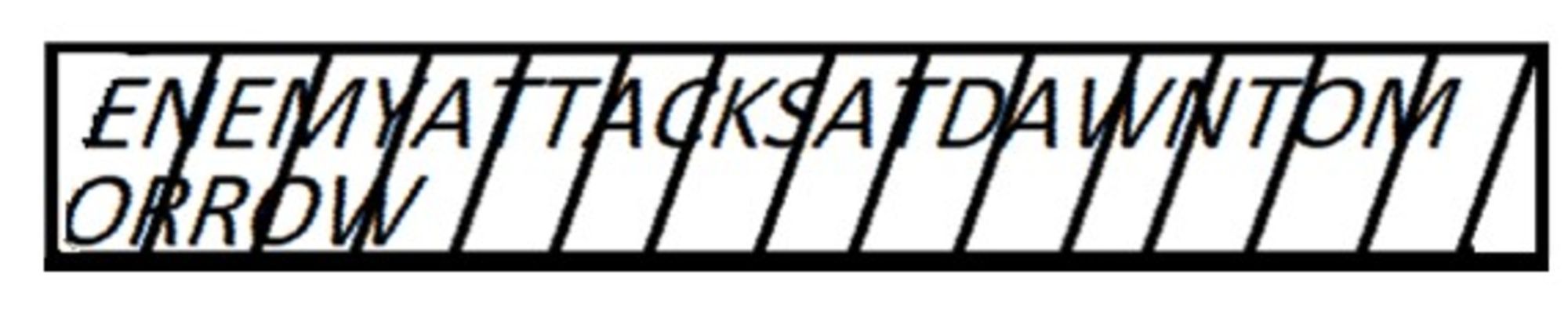
Since Plutarch’s description indicates the likelihood that the whole strip was used for writing, at least some of the letters on the strip would have been written whole and on a complete piece of strip. These letters would have remained intact and recognisable once the strip was unwrapped from the scytale. Yet, since some of the letters on the strip would have been written overlapping the edges of the strip, these letters would not have remained intact once the strip was unwrapped from the scytale. And indeed, according to Aulus Gellius, this is what happened in practice: the unrolling of the strip made the letters imperfect and broken (see Figure 4):
The unrolling of the thong made the letters imperfect and broken, and their parts and strokes were divided and separated. Therefore, if the thong fell into the hands of the enemy, nothing at all could be made out from the writing […]. (Aulus Gellius, Attic Nights, 17.9.12-14).
If the strip from Figure 3 was unwrapped from the scytale, the strip would look like the following figure (Figure 5). In this figure the strip is cut into pieces to show the difference between the partial and complete letters.
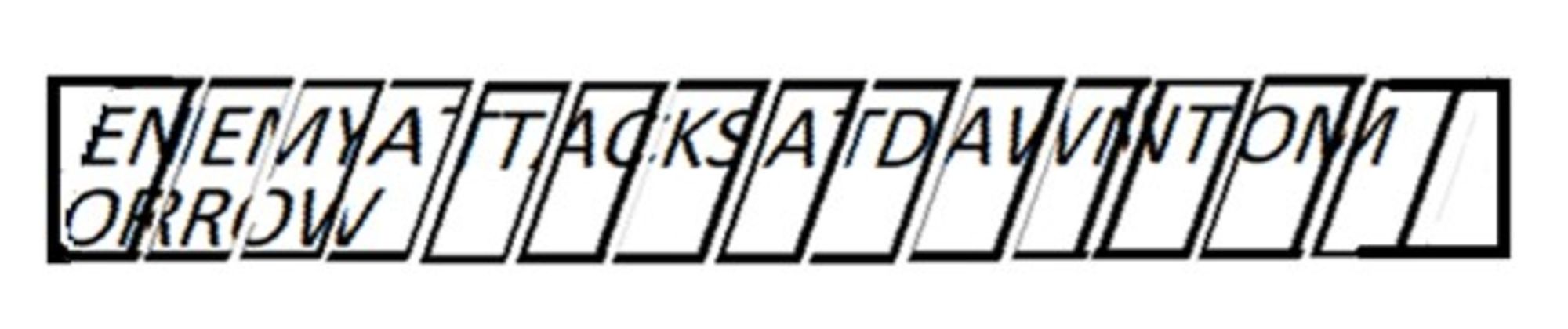
Although neither Plutarch nor Aulus Gellius mentions it, the message could have been written in either plaintext (normal non-encrypted text) or ciphertext (encrypted text) with the latter option making the message doubly secret and, therefore, doubly secure. However, nothing in their descriptions proves that the text was written in cipher. It will, therefore, be presumed that the scytale messages were written in plaintext. After a message was written on the strip of parchment or papyrus, the strip was then unwrapped from the scytale stick (Plutarch, Life of Lysander, 19.5; Aulus Gellius, Attic Nights, 19.7.6-10). By unwrapping the text strip from the scytaleall letters in the original message were transposed to a different position, as Plutarch and Aulus Gellius described. Thus, according to Plutarch, when a general in the field received a scytale message:
He, [could not] get any meaning out of it, — since the letters have no connection, but are disarranged […] (Plutarch, Life of Lysander, 19.7).
While Aulus Gellius additionally mentions partial and broken letters:
the unrolling of the thong made the letters imperfect and broken, and their parts and strokes were divided and separated (Aulus Gellius, Attic Nights, 17.9.12-13).
This transposing of the letters in the message makes the scytale the first theoretical military transposition cipher known in history, an encryption technique whereby the normal sequence of letters of a plaintext (non-encrypted text) is rearranged.[5] As Singh states:
[A] form of transposition is embodied in the first ever military cryptographic device, the Spartan scytale.[6]
We can see from the reconstruction above just how challenging it would have been to attempt to reconstruct the original text from this scrambled ciphertext. It would certainly not be impossible, but without a scytalerod of the same size as the one used in the original encryption it would have been time-consuming. A good modern parallel might be the paper shredder, which offers one way of ‘encrypting’ or scrambling a confidential source text. With patience, skill, and time, the original text can be reconstructed from the shredded strips of paper. The advantage of the scytale device, however, is that it offers the opportunity for that reconstruction to be managed much more quickly and easily.
Plutarch’s and Aulus Gellius’ descriptions do not prove that scytalaewere used in practice for secret communication. Also, it must be borne in mind that Plutarch is not offering us an eye-witness testimony of the scytale as a Spartan cryptograph in these descriptions: Plutarch wrote about the sending of secret scytale messages in the 2nd century CE, about 600-700 years after famous Spartans like Lysander, Clearchus, and Agesilaus allegedly received these encrypted scytale-messages – lived. Therefore, we cannot know with certainty how much of Plutarch’s and Aulus Gellius’ stories are true. Perhaps Plutarch believed the messages were sent in the secret way that he described (Plutarch, Life of Lysander, 19.5-7). He may have had sources that are lost to us, including the work of the 4th-century BCE Greek historian Theopompus. However, another possibility includes that the method was invented by Plutarch to enhance his stories. And Aulus Gellius has later followed Plutarch (Aulus Gellius, Attic Nights, 17.9-5). Yet, with Plutarch’s description we have the earliest theoretical transposition cipher in history: a cipher systems that keeps reappearing and developing throughout the ages until modern day. This point has previously been overlooked by other scholars. So, we must give Plutarch some credit – even though the description of the scytale as a Spartan cryptography, and the stories Plutarch tells us may be (partially) invented by the author himself.
[1] Besides its use in a military context, other ancient uses of cryptography and steganography include its use in love letters, its use to increase the level of mysticism in inscriptions, and its use in magical and religious texts (Ausonius, Epistles, 28.21-22; Ovid, Ars Amatoria, 3.627-630; Pliny the Elder, Natural History, 26.39 (62)). See also: Pieprzyk, Hardjono, and Seberry 2013, 6; Waldstein & Wisse 1995; Wisse 1979; 1980; 1981; 1982; 1983; 1989; 1990.
[2]Perrin 1916, 287; Poe 1841, 33.
[3]Kahn 1967, 75-76; Mollin 2005, 9; Smith 1955, 16.
[4] Jeffery 1961, 57; Sherwood 2006, 536-537.
[5] Bauer 2007, 382; Reinke 1962, 113; Singh 1999, 5.
[6] Singh 1999, 7.
Bibliography:
Bauer, F. L. (2007). Decrypted Secrets: Methods and Maxims of Cryptology. Berlin/ Heidelberg/ New York: Springer-Verlag.
Jeffery, L. H. (1961). The Local Scripts of Archaic Greece: A Study of the Origin of the Greek Alphabet and its Development from the eighth to the fifth centuries B.C. Oxford: Clarendon Press.
Kahn, D. (1967). The Codebreakers: The Comprehensive History of Secret Communication from Ancient Times to the Internet. London: Weidenfeld and Nicolson.
Mollin, R. A. (2005). Codes: The Guide to Secrecy From Ancient to Modern Times. Boca Raton/ London/ New York/ Singapore: Chapman & Hall/CRC - An imprint of Taylor and Francis Group.
Perrin, B. (1916). Plutarch: Lives (Volume IV: Alcibiades and Coriolanus, Lysander and Sulla; Loeb Classical Library 80). Cambridge (Massachusetts): Harvard University Press.
Pieprzyk, J., Hardjono, T., & Seberry, J. (2013). Fundamentals of Computer Security. Berlin: Springer Science & Business Media.
Poe, E. A. (1841). A Few Words on Secret Writing. Graham’s Magazine, 19, 33-38.
Reinke, E. C. (1962). Classical Cryptography. The Classical Journal, 58 (3), 113-121.
Sherwood, A. N. (2006). Papyrus and Parchment. In: Wilson, N. G. (ed.), Encyclopedia of Ancient Greece. New York/ London: Routledge - An Imprint of Taylor and Francis Group, 535-537.
Singh, S. (1999). The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography. London: Fourth Estate.
Smith, L. D. (1955). Cryptography: The Science of Secret Writing: History and Modern Use of Codes and Ciphers, together with 151 Problems and their Solutions. Mineola: Courier Corporation: Business and Economics/Dover Publications.
Waldstein, M., & Wisse, F. (1995). The Apocryphon of John: Synopsis of Nag Hammadi Codices II, 1, III, 1, and IV, 1, with BG 8502, 2. Leiden: Brill.
Wisse, F. (1979). Language Mysticism in the Nag Hammadi Texts and in Early Coptic Monasticism I: Cryptography. Enchoria: Zeitschrift für Demotistik und Koptologie, 9, 101-120.
Wisse, F. (1980). Textual Restorations in On The Origin of the World. The Bulletin of the American Society of Papyrologists, 17 (1-2), 87-91.
Wisse, F. (1981). The Opponents in the New Testament in light of the Nag Hammadi Writing. In: Barc B. (ed.), Colloque international sur les textes de Nag Hammadi : Québec, 22-25 août 1978. Québec/ Louvain: Presses de l'Université Laval/ Editions Peeters, 99-120.
Wisse, F. (1982). The Profile Method for the Classification and Evaluation of Manuscript Evidence, as applied to the continuous Greek text of the Gospel of Luke. Grand Rapids: Eerdmans.
Wisse, F. (1983). Prolegomena to the study of the New Testament and Gnosis. In: Logan, A. & Weddeburn, A. (eds.), The New Testament and gnosis: essays in honour of Robert McL. Wilson. Edinburgh: T. & T. Clark, 138-145.
Wisse, F. (1989). The Nature and Purpose of Redactional Changes in Early Christian Texts: The Canonical Gospels. In: Petersen, W. (eds.): Gospel Traditions in the Second Century: Origins, Recensions, Text, and Transmission. Notre Dame: University of Notre Dame Press, 39-53.
Wisse, F. (1990). Pseudo-Liberius, Oratio Consolitaria de morte Athanasii. Le Muséon, 103 (1-2), 43-65.






