
This article relates to episode 6 in the series ‘Cyber Security in the Ancient World’. Episode 6 and 7 discuss ancient fire signalling. In this episode (6) we will discuss Greek fire signalling. In the next episode (7) we will discuss Roman fire signalling.
From accounts of Near Eastern, Greek (and later Roman) history starting in the archaic period, for example, we know that both normal (that is, non-encrypted) and simple encoded or encrypted messages could be sent over long distances by means of fire signals as discussed in a wide range of classical sources.[1]
Thus, to take just one salient example from this extensive list, Aeschylus in his Agamemnondescribes how Clytaemnestra received word from Agamemnon returning from Troy by means of beacons signals that were fast and efficiently sent from one station and one hilltop to the next (Aeschylus, Agamemnon, 281-283).
As it was only possible to send one prearranged message using this archaic system of fire signalling, communicating parties needing to communicate on urgent matters faced significant limitations (Polybius, Histories, 10.43-5-6). The 4th century BCE Greek military author Aeneas Tacticus accordingly invented a method for fire signalling in which water clocks and torches were used, whereby a series of messages could be sent back and forth between distant mountain tops. Aeneas Tacticus’ system is discussed in a now lost work on military preparations, but its basic design has been handed down to us via Polybius (Histories, 10.44).
According to Polybius, Aeneas Tacticus discussed how communicating parties could send messages by using water clocks and torches. Both parties would fill large vessels of the same size with a cork at the bottom with water. Then they would take a rod graduated in sections – each clearly marked off from the next. In each section there would be written the most evident and ordinary events that occurred in war (e.g., ‘Enemy approaching with ships from the west’). The rod was placed into the vessel. When the two parties wanted to send a message, they would first wave torches to attract each other’s attention. Then they would pull out the corks from the vessels to let the water run out. In this way the rods would sink. When the intended message on the rod had reached the top of the vessel, the sending party would wave a torch again to let the receiving party know that they had to pull the cork back into the vessel and check the intended message.
If all worked well, the receiving party could then read the message. What Polybius and (we infer from the attributions to Aeneas Tacticus here) what Aeneas Tacticus also described was a highly inventive mode of long-distance communication. Indeed, it has been described as the earliest form of telegraphy used in the world and the most sophisticated system for secret communication discussed by Polybius (see Figure 1).[2] It is suggested by the 2nd-century CE author Polyaenus that the Carthaginians used a similar method successfully: Polyaenus implies that by sending (secret) fire signals the Carthaginians were always provided in the most rapid way with what they needed in their warfare (Polyaenus, Stratagems of War, 6.16).[3]
Experiments in archaeology carried out by Woolliscroft in 2001 have shown the Carthaginian system to be feasible (and potentially also Aeneas Tacticus’ similar system, as reconstructed by Polybius).[4] Although at first, doubts were raised as to whether the ancient Greeks and Romans would have had the engineering skills to build and use such a system, Woolliscroft showed the potential and usefulness of these ancient fire signalling systems. However, there are two significant downsides to Aeneas Tacticus’ method. First, it would have been extremely difficult to let the two water clocks run exactly parallel, as Woolliscroft argues:
It is in fact surprisingly difficult to make water run out of two vessels at exactly the same rate and even tiny inaccuracies become more serious the longer the clock is left running.[5]
Because of this it is hard to believe that Aeneas Tacticus’ mechanism ever functioned well. What is more, with this method it remains the case that only pre-arranged messages could be transferred between the communicating parties something that Polybius acknowledged himself. He states that it would have been impossible to communicate by using Aeneas Tacticus’ method, if anything unexpected occurred (Polybius, The Histories, 10.45.1-5).
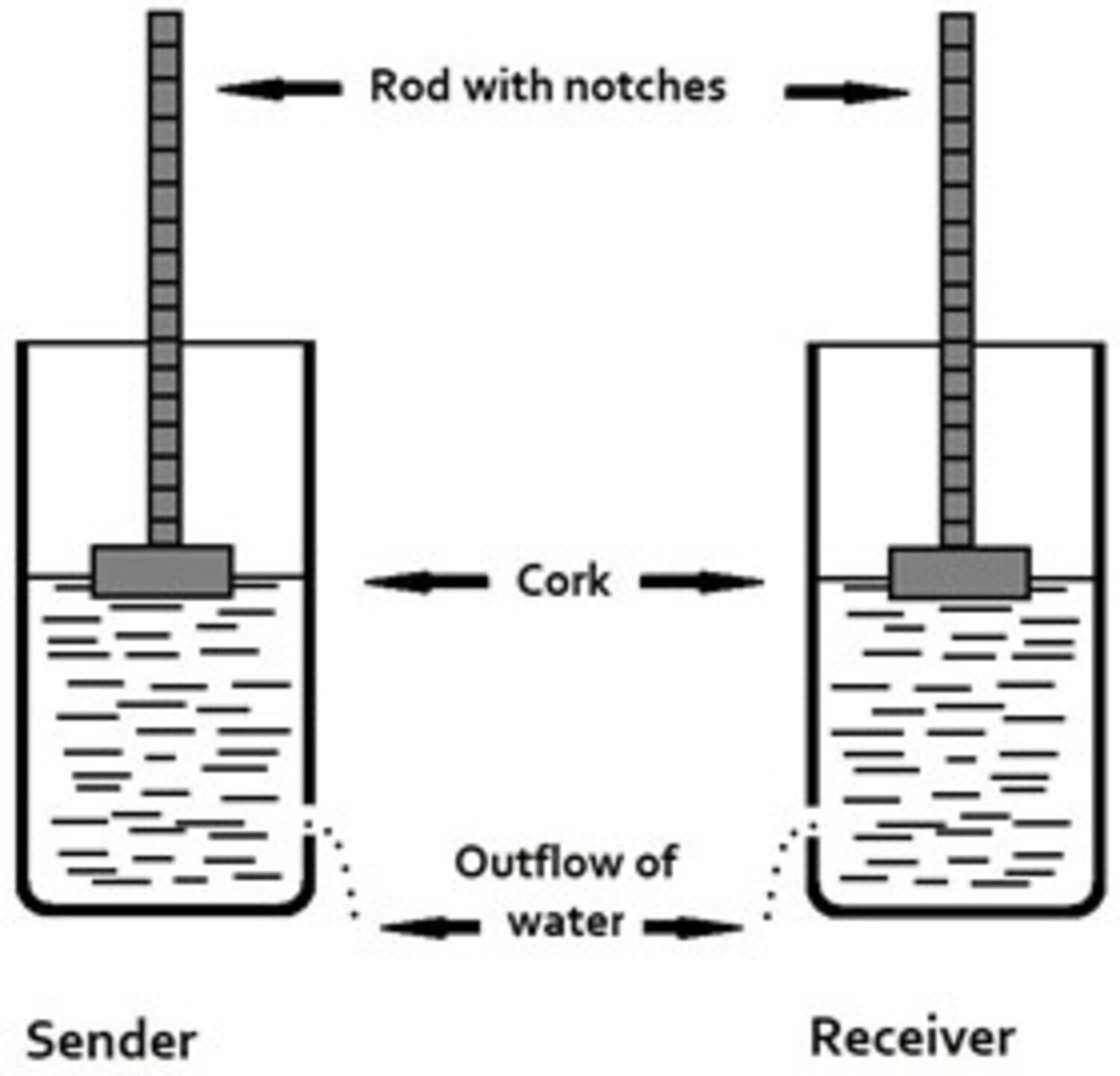
Indeed, Polybius here shows that it would have been impossible to communicate by using Aeneas Tacticus’ method if anything unexpected were to have occurred. Polybius, therefore, believed Aeneas Tacticus’ method to have been a slight advance over the earliest and simplest beacon signals, yet the system was still quite rudimentary as he argues – since still only a series of prearranged messages could be sent. Therefore, Polybius decided to improve upon this method by developing it into a more sophisticated system of fire signalling: a system capable of dispatching with accuracy any kind of message. Thus, Polybius describes how to take five tablets – and write on these tablets all letters of the (Greek) alphabet from alpha to omega, and two sets of five torches. The dispatcher of the message would then raise the first set of torches on the left side indicating which tablet was to be consulted (1-5). Then he would have raised the second set of torches on the right to indicate what letter on the tablet the receiver should write down (Polybius, The Histories, 10.45.6-12).[6]
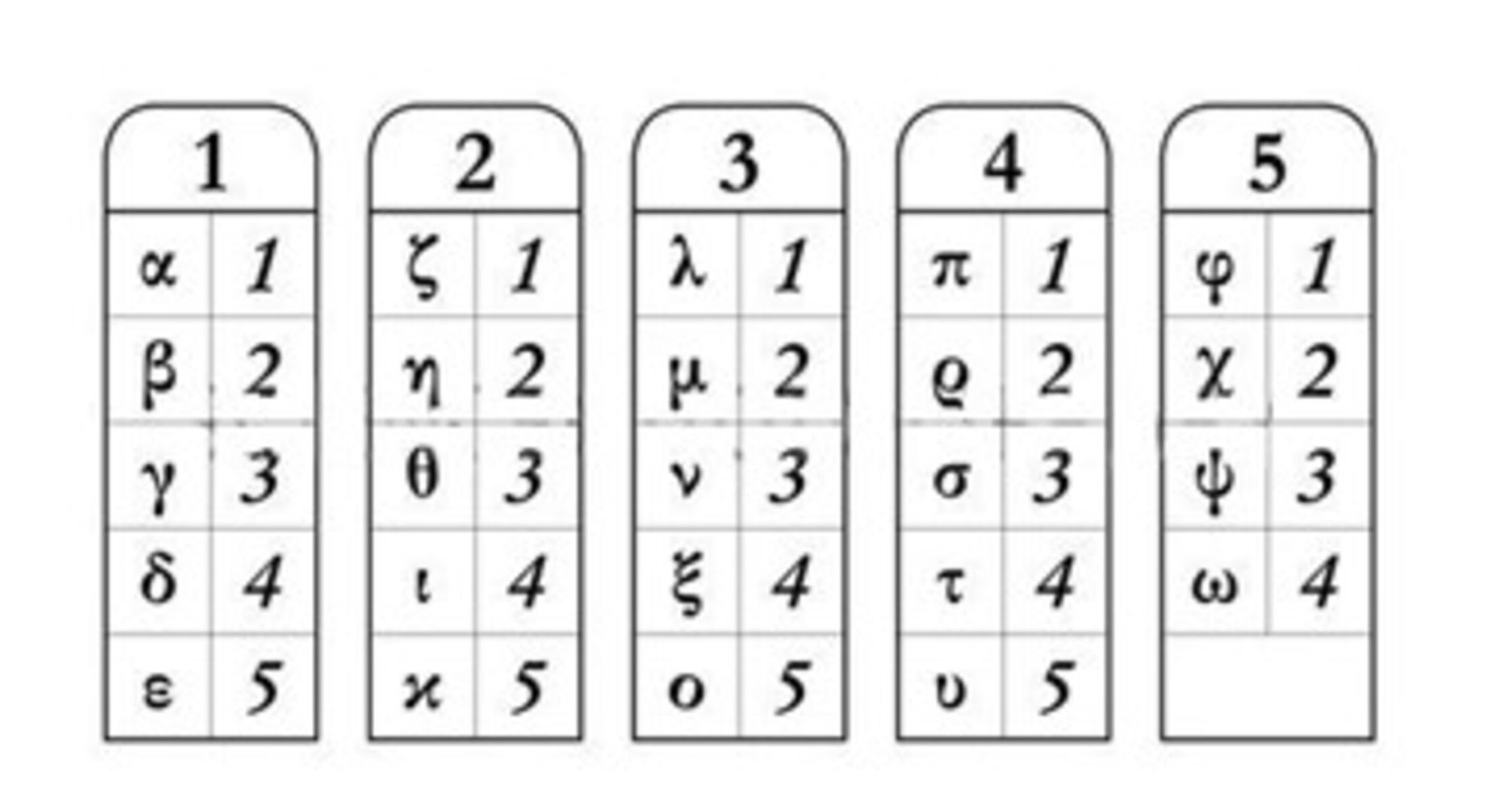
Like Aeneas Tacticus, Polybius still uses torches, but replaces the water clocks with tablets on which the letters of the Greek alphabet were written (see Figure 2). One could then send messages letter by letter, whereby each fire signal represented one letter. Although Polybius’ method was still extremely laborious, it was clearly a significant improvement over Aeneas Tacticus’ method, since in Polybius’ system no water clocks were involved that had to run parallel. What is more, when using Polybius’ system every possible alphabetic message could be sent between communicating parties, instead of only a series of prearranged messages. This is made possible using the alphabetic tablets that form the basis for what is known in modern cryptography as the ‘Polybius square’ – which some historians of cryptography (erroneously) believe to have been invented by Polybius himself[7]
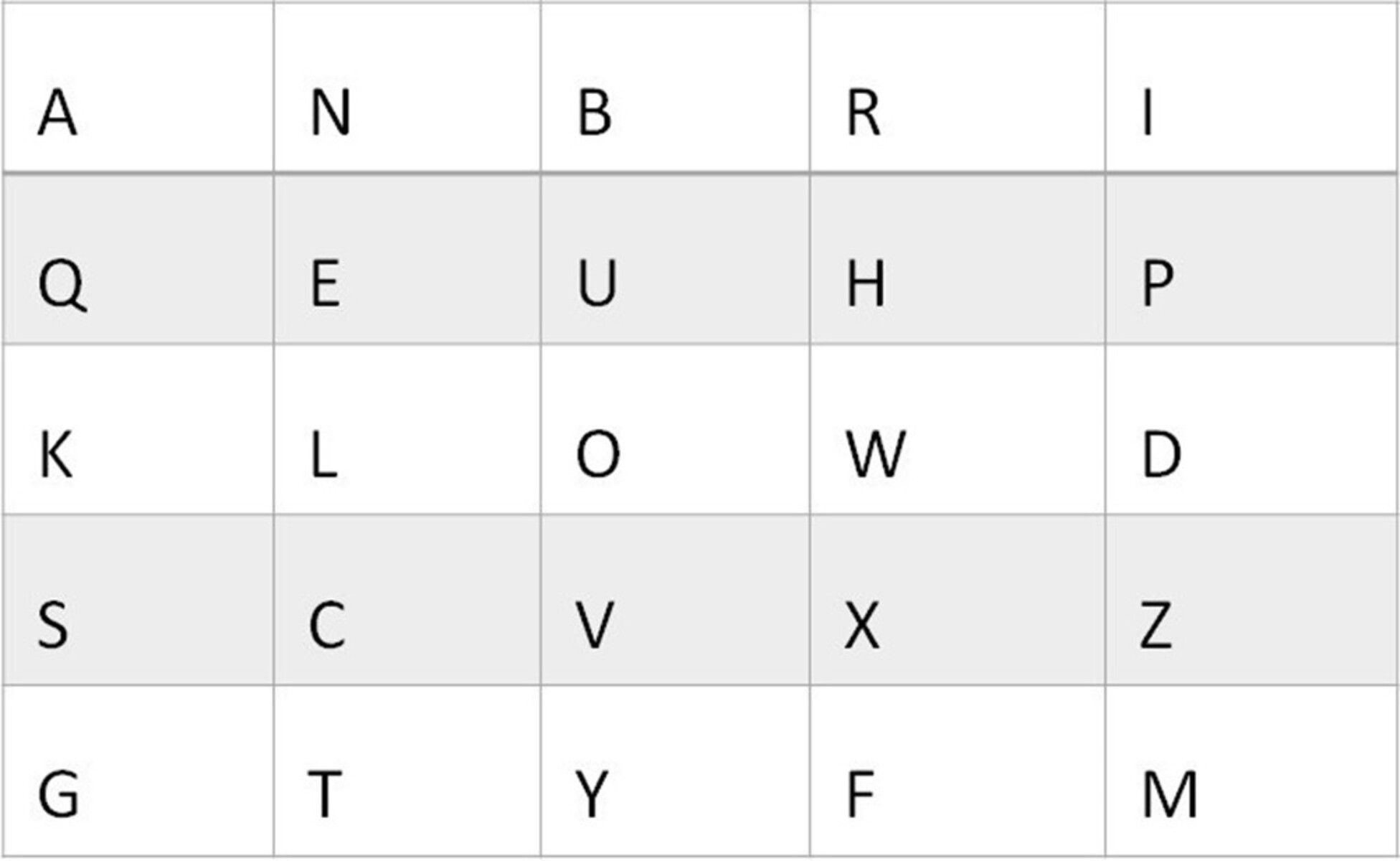
The ‘Polybius square’ is a square which consists of five rows and five columns – giving 25 cells. In these cells the 26 letters of a modern alphabet are written in their normal order from left to right, and top to bottom (see Figure 3). Hereby, following an idiosyncratically Latin rather than Greek tradition, the letters ‘I’ and ‘J’ are usually placed in the same block.[8]All rows and columns in the square have a number. In a basic square these are the numbers one to five for both rows and columns. Every letter in the square thus gets a coordinate. The letter ‘A’, for example, can be found in the first row on the first column, which gives the coordinate 1-1, written as ‘11’.[9] In this way, all the letters in the square have a coordinate between ‘11’ (A) and ‘55’ (Z). The coordinates can be compared to the place of the letters on Polybius’ tablets.

A modern message that is sent by use of a Polybius square, looks like a series of numbers. The message ‘SEND MORE TROOPS BEFORE MIDNIGHT’, for example, would appear as the following numerical sequence:
43 15 33 14 32 34 42 15 44 42 34 34 35 43 12 15 21 34 42 15 32 24 14 33 24 22 23 44
Since every coordinate contains two numbers – one for the row and one for the column – an encrypted text is created that is twice as long, as the non-encrypted text.[10] To decipher the message, the recipient would take a Polybius square, look for the coordinates in the square, and check which letters correspond to these coordinates – using the square as the ‘key’ with which to decrypt the encoded text. The Polybius square has reportedly been used for simple cryptographic communications in this way by the British army in the Boer War, and by both the British and German armies in the First and Second World Wars.[11]
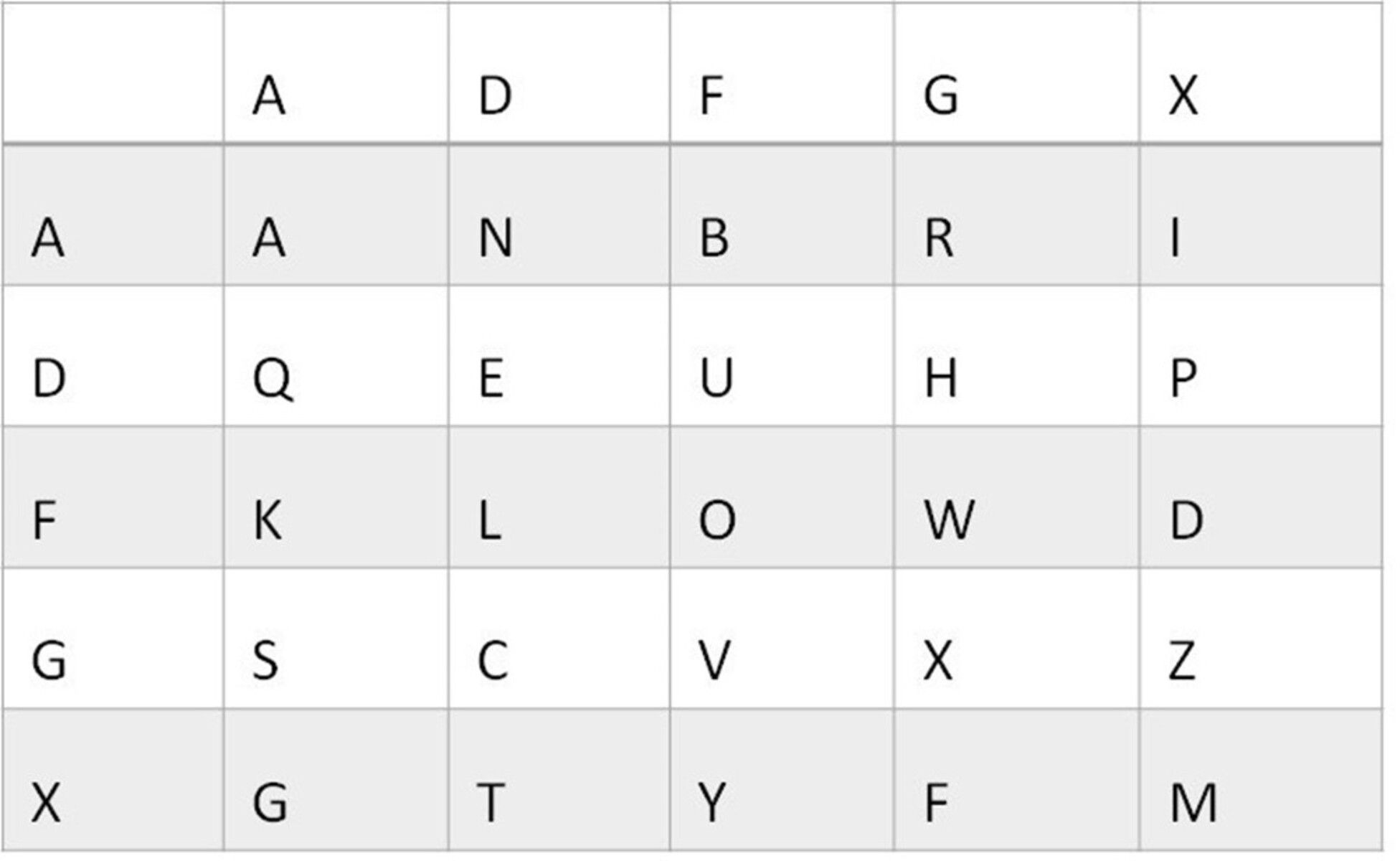
Yet, the basic cryptographic operating principles upon which the Polybius square and its encryptions works can also be seen to be employed as the basis for other more sophisticated modern cryptographic methods. In the last year of the First World War, for example, the German military intelligence services used the Polybius square in their ADFGX and ADFGVX-ciphers,[12] named after the only five, and later the only six, alphabetic letters that appeared in the ciphertext.[13] Messages encrypted with the ciphers were transmitted by Morse code so these six letters were chosen to minimise transmission errors, since the letters sound very different from one another in Morse code. In March 1918, the first of the cipher systems was introduced: the ADFGX-cipher. This cipher used a Polybius square of 5x5. This square was filled with 26 letters of the German alphabet in random order, and the ensuing distribution pattern – the encryption key – shared between sender and recipient (see Figure 4 and 5).[14] This scrambling of letters is a key characteristic of the modern Polybius square (see Figures 3 and 4) – something that we cannot see in the ancient accounts of Polybius’ system in which the letters never seem to have changed position.[15]
The rows and columns of the Polybius square used for the cipher were then labelled with the letters ‘A’, ‘D’, ‘F’, ‘G’, and ‘X’ to produce a coordinate for each of the plaintext letters: in this case, for example, the plaintext letter ‘Y’, was encrypted as ‘XF’ (see Figure 5).
In this way, a ciphertext was created that was twice as long as the plaintext, and that only contained the letters ‘A’, ‘D’, ‘F’, ‘G’, and ‘X’. The plaintext message ‘Send weapons quickly’, for example, would have been substituted into the following ciphertext:
GA DD AD FX FG DD AA DX FF AD GA DA DF AX GD FA FD XF
It is relevant to mention here that the aforementioned step is only the first stage of ADFGX encryption. This is followed by columnar transposition before sending the message. The addition of this second element makes the system a combination of a transposition and a substitution cipher.[16] One of the characteristics of a Polybius square is that the ciphertext only consists of these five distinct characters. The ADFGX-cipher has this distinctive Polybius square characteristic, potentially making it identifiable to enemy agents as a code based on Polybius square principles and, thus, giving those who intercepted it the opportunity to decode it easily.
In June 1918, three months after the introduction of the first ADFGX-cipher, the Germans added an extra row and column to the Polybius square that was used for the cipher to create a 6x6 grid to increase the level of sophistication of the method. Extending the grid meant that an extra letter was required to create the ciphertext. The letter V was chosen for this since this letter sounds different from the five other letters in Morse code. The newly created cipher was accordingly (and perhaps unimaginatively) called the ADFGVX-cipher.[17] It worked in the exact same way as its predecessor the ADFGX-cipher. The ADFGX- and ADFGVX-ciphers were the most advanced cipher systems that the German military intelligence used during the First World War.[18] In fact, despite being based on the encryption principles of the Polybius square and sharing common features with an ancient Greek fire signalling device invented more than two thousand years earlier, they turned out (according to military historians and modern cryptographers) to be amongst the toughest ciphers known in military secret communication until the end of the First World War.[19]
The fact that we see the same basic technologies of secret communication exhibited in antiquity – in this case by Aeneas Tacticus’ and Polybius’ systems for fire-signalling – and again in the First World War – in the ADFGX and ADFGVX-ciphers – helps us to appreciate more fully the practical efficiency and value of those basic technologies and techniques as they would have been used in antiquity. Indeed, the fact that ancient core principles of cryptography are still in use in some form in 20thand even 21st century methods for secret communication demonstrates that these methods would and could have worked well in antiquity.
[1] Aeneas Tacticus, How to Survive Under Siege, 4.1; 4.5-6; 6.1-6-7; 7.1-7.4; 10.25-26; Apollodorus, Epitome, 5.19; Aristotle, On the Universe, 398a; Aeschylus, Agamemnon, 7-9; 20-29; 278-350; Appian of Alexandria, The Civil Wars, 1.6.51; 12.66; The Spanish Wars, 6.15.90-92; Caesar, The Gallic War, 2.33; 3.65-67; 7.3; The Civil War, 3.65; Cicero, The Verrine Orations, 2.5.35; Diodorus Siculus, Library of History, 18.57.5; 19.17.7; Flavius Josephus, Books of the History of the Jewish War against the Romans, 4.10.5; Frontinus, Stratagems, 2.5.16; Herodotus, Histories, 6.115; 7.183; 9.3; Homer, Iliad, 4.275-276; 5.770-771; 18.203-214; Julius Africanus, Kestoi, 77; Livy, History of Rome, 22.19.6; Maurice, Strategikon, 7.2.10; Onasander, The General, 25.3; Pausanias, Description of Greece, 2.25.2; Pliny, Natural History, 35.48 (14); Polybius, The Histories, 1.19; 8.28-29; 10.42-47; Polyaenus, Stratagems of War, 4.19.2; 6.16.2; Simonides, Elegies, 130; Suetonius, Life of the Caesars 3. Tiberius, 65; Thucydides, History of the Peloponnesian War, 1.63; 2.94; 3.22; 3.80; 4.42. 4.111; 8.95; 8.102; Vegetius, The Military Institutions of the Romans, 3.5.25l; Virgil, Aeneid 10.454; 11.526; The Eclogues, 8; 59; Xenophon, Hellenica, 1.1.1-4; 2.1.27; 5.1.27; 6.2.33-34. See also: Aschoff 1984; Dvornik 1974, 31-33; Hyde 1915; Sheldon 1987, 135; Sheldon 2005, 127; Woolliscroft 2001, 159-171.
[2] D’Agapeyeff 1939, 16-17; Dvornik 1974, 42-43; Hunter & Handford 1927, 120; 122-123; Liddel 2018, 127-128; Oldfather 1923, 46-47; Rihll 2018, 281-287.
[3] See also Dvornik 1974, 56; Sheldon 1987, 28.
[4] Woolliscroft 2001; Sheldon 2005, 205.
[5] Woolliscroft 2001, 32, see already Hunter & Handford 1927, 120.
[6] See for a parallel from Roman times: Julius Africanus, Kestoi, 77.
[7] Smith 1955, 16; Kahn, 1996a, 76-77; 82-83; 1996b; Mollin 2005, 9-10; Mollin 2006, 89.
[8] Kahn 1996a, 83; Lunde 2012, 78-79; Mollin 2006, 90.
[9]Mollin 2006, 90; Lunde 2012, 78-79; Kahn 1996a, 83.
[10] Mollin 2005, 1; Reba & Shier 2015, 480.
[11] Kahn 1996a, 83; 1996b; Lunde 2012, 78-79; Mollin 2006, 90; Van Tilborg 2006, 32.
[12] Van Tilborg 2006, 32.
[13] Childs 1919, 13; Dooley 2016, 65; Klima & Sigmon 2012, 55; Mollin 2005, 1; Reba & Shier 2015, 480.
[14] The German alphabet has 30 letters: 26 letters as in the English alphabet and 4 more signs (ä, ö, ü and ß). These signs were left out in the Polybius square.
[15] If Polybius had decided to change the order of letters on his tablets (regularly), the method would have become more secure. Yet, in this case communicating parties would have had to send each other the key information on the changed order of letters.
[16] See for columnar transposition ciphers e.g.: Bauer 2013, 128-130; 136; 2017, 217-222; Bishop 2003, 19; Childs 1919, 13; Churchhouse 2003, 45-46; Collard 2004; Dooley 2016, 62-65; Kahn 1996a, 535; 539; Stamp & Low 2007.
[17] Klima & Sigmon 2012, 55-57.
[18] Mollin 2000, 12.
[19] Churchhouse 2002, 45-46; Kahn 1996a, 334; 535-539; Mollin 2000, 12.
Bibliography:
Aschoff, V. (1984). Geschichte der Nachrichtentechnik: Beiträge zur Geschichte der Nachrichtentechnik von ihren Anfängen bis zum Ende des 18. Jahrhunderts. Berlin/ Heidelberg/ New York/ Tokyo: Springer-Verlag.
Bauer, C. P. (2013). Secret History: The Story of Cryptology. Boca Raton/ London/ New York: CRC Press - An Imprint of Taylor and Francis Group.
Bauer, C. P. (2017). Unsolved! The History and Mystery of the World's Greatest Ciphers from Ancient Egypt to Online Secret Societies. New Jersey/ Woodstock: Princeton University Press.
Bishop, D. (2003). Introduction to Cryptography with Java Applets. Surbury/ Boston/ Toronto/ London/ Singapore: Jones and Bartlett Publishers.
Childs, J. R. (1919). War Department Office of the Chief Signal Officer, Washington: German Military Ciphers from February to November 1918. Technical Paper of the Intelligence Section War Plans and Training Division. Retrieved from: NSA Online Database https://www.nsa.gov/Portals/75/documents/news-features/declassified-documents/friedman-documents/correspondence/ACC39301/41782529082158.pdf
Churchhouse, R. F. (2002). Codes and Cipher: Julius Caesar, the Enigma and the Internet. Cambridge: Cambridge University Press.
Collard, B. (2004). Les Languages secrets dans l'Antiquité Gréco-Romaine. Introduction Générale, Plan et Bibliographie par Brigitte Collard. Retrieved from : Folia Electronica Classica (Louvain-la-Neuve) – Numéro 7 janvier - juin 2004. Retrieved from: http://bcs.fltr.ucl.ac.be/FE/07/CRYPT/Intro.html
D'Agapeyeff, A. (1939). Codes and Ciphers - A History of Cryptography. Oxford / London / New York/ Toronto: Oxford University Press.
Dooley, J. F. (2016). Codes, Ciphers and Spies: Tales of Military Intelligence in World War I. New York: Copernicus Books - An imprint of Springer Nature.
Dvornik, F. (1974). Origins of Intelligence Services: The Ancient Near East, Persia, Greece, Rome, Byzantium, the Arab Muslim Empires, the Mongol Empire, China, Muscovy. New Brunswick/ New Jersey: Rutgers University Press.
Hunter, L., & Handford, S. (1927). Aineiou Poliorkētika: Aeneas on Siegecraft. Oxford: Clarendon Press.
Hyde, W. W. (1915). The Mountains of Greece. The Bulletin of the Geographical Society of Philadelphia, 13, 1-16; 47-64; 110-126.
Kahn, D. (1996a).The Codebreakers: The Comprehensive History of Secret Communication from Ancient Times to the Internet (2nd edition, revised). London: Weidenfeld and Nicolson.
Kahn, D. (1996b). The History of Steganography. In: Anderson, R. (ed.), Information Hiding: First International Workshop, Cambridge, U.K., May 30 - June 1, 1996. Proceedings, Volume 1, 1-6. Cambridge: Springer-Verlag.
Klima, R., & Sigmon, N. (2012). Cryptology: Classical and Modern with Maplets. Boca Raton/ London/ New York: Chapman and Hall/ CRC.
Lunde, P. (2012). The Secrets of Codes: Understanding the World of Hidden Messages. San Francisco: Weldon Owen.
Mollin, R. A. (2000). An Introduction to Cryptography.Boca Raton/ London/ New York/ Washington: Chapman & Hall/ CRC.
Mollin, R. A. (2005). Codes: The Guide to Secrecy From Ancient to Modern Times. Boca Raton/ London/ New York/ Singapore: Chapman & Hall/CRC - An imprint of Taylor and Francis Group.
Mollin, R. A. (2006). An Introduction to Cryptography. Second editon. Boca Raton/ London/ New York/ Washington: Chapman & Hall/ CRC - An imprint of Taylor and Francis Group.
Oldfather, W. A. (1928). Introduction and Notes. In: Illinois Greek Club, Aeneas Tacticus, Asclepiodotus, Onasander. (Volume 156 Loeb Classical Library). Cambridge (Massachusetts): Harvard University Press.
Reba, M. A., & Shier, D. R. (2015). Puzzles, Paradoxes, and Problem Solving: An Introduction to Mathematical Thinking. London/New York/ Boca Raton: CRC Press - An imprint of Taylor and Francis Group.
Rihll, T. E. (2018). Technology in Aineias Tacticus: Simple and Complex. In: Pretzler, M. & Barley, N. (eds.), Brill's Companion to Aineias Tacticus. Leiden /Boston: Brill, 265-289.
Sheldon, R. M. (1987). Tinker, Tailor, Caesar, Spy: Espionage in Ancient Rome. Ann Arbor: UMI Dissertation Information Service.
Sheldon, R. M. (2004). Intelligence Activities in Ancient Rome: Trust in the Gods, but Verify. London/ New York: Routledge - An Imprint of Taylor and Francis Group.
Sheldon, R. M. (2005; first edition second print). Intelligence Activities in Ancient Rome: Trust in the Gods, but Verify. London: Frank Cass.
Smith, L. D. (1955). Cryptography: The Science of Secret Writing: History and Modern Use of Codes and Ciphers, together with 151 Problems and their Solutions. Mineola: Courier Corporation: Business and Economics/Dover Publications.
Stamp, M. & Low, R. M. (2007). Applied Cryptanalysis: Breaking Ciphers in the Real World. San Jose: Wiley Interscience.
Van Tilborg, H. C. (2006). Fundamentals of Cryptology: A Professional Reference and Interactive Tutorial by Henk C. A. van Tilborg, Eindhoven University of Technology, The Netherlands (second edition). Boston/ Dordrecht/ London: Kluwer Academic Publishers.
Woolliscroft, D. I. (2001). Roman Military Signalling. Stroud: Tempus.






