
This article relates to episode 8 in the series ‘Cyber Security in the Ancient World’.
The only cryptographic system (a system for encrypting messages rather than hiding them) that seems to have been used in Roman communications, according to our available sources, is the so-called Caesar cipher named after Julius Caesar by modern cryptographers since he is supposed to have invented and used this technique. Caesar seems to have used his cipher to communicate with his generals over long distances – similar to the theorical Spartan use of the scytale. The Caesar cipher is often regarded as a simple substitution technique for encryption, whereby each letter of a plaintext is replaced by a letter that can be found a fixed number of positions down the alphabet.[1]
In other words, in the ciphertext alphabet used for encryption and decryption there is always one shift of letters for the entire message – for example a right shift of three as in the case of Caesar’s use of the cipher (Aulus Gellius, Attic Nights, 17.9.2-5; Cassius Dio, Roman History, 40.9.4; Suetonius, Lives of the Caesars 1. The Deified Julius, 56.6). According to Cassius Dio this worked in the following way:
It was his [Caesar’s] usual practice, whenever he was sending a secret message to any one, to substitute in every case for the proper letter of the alphabet the fourth letter beyond, so that the writing might be unintelligible to most persons (Cassius Dio, Roman History, 40.9.4).
And Suetonius adds that:
There are […] letters […] to his [Caesar’s] intimates on private affairs, […] [when] he had anything confidential to say, he wrote it in cipher, that is, by so changing the order of the letters of the alphabet that not a word could be made out (Suetonius, Lives of the Caesars 1. The Deified Julius, 56.6).
Finally, Aulus Gellius mentions the names of two of Caesar’s correspondents with whom Caesar communicated in cipher: his generals Oppius and Balbus:
There are […] letters of Gaius Caesar addressed to Gaius Oppius and Cornelius Balbus who had charge of his affairs in his absence. In certain parts of [the] letters there are found individual characters which are not connected to form syllables, but apparently are written at random; for no word can be formed from those letters (Aulus Gellius, Attic Nights, 17.9.1-2).
Significantly, the term ‘Caesar cipher’ is a term that only appears in modern books on cryptography.[2] Caesar himself did not discuss the cipher (nor its potential name) in any of his surviving works. Yet, descriptions of the cipher (again without its potential name) come from antiquity (Aulus Gellius, Attic Nights, 17.9.1-6; Suetonius, Life of Julius Caesar, 56.6-7; Cassius Dio, Roman History, 40.9.3).[3]
Dio argues that Caesar’s secret letters were unintelligible to most – but not all – people (Roman History, 40.9.4). Suetonius in turn describes letters to Caesar’s intimates on confidential affairs – in both a private context and in his capacity as a general – as having been written in cipher to prevent Caesar’s enemies from reading the messages if they were intercepted (Lives of the Caesars 1. The Deified Julius, 56.6).
From Suetonius’ and Dio’s descriptions it becomes clear that Caesar’s encryption worked by substituting every alphabetic letter of a plaintext for the alphabet letter that could be found three places further down the alphabet (moving from the left to the right): e.g. ‘A’ became ‘D,’ ‘B’ became ‘E’ and so on with the rest. Aulus Gellius mentions the names of two of Caesar’s correspondents with whom Caesar communicated in cipher: his generals Oppius and Balbus (Attic Nights, 17.9.1-2).
In addition to sending secret and/or encrypted letters to his generals, Caesar would most likely also have communicated in cipher with his scouts and spies: the exploratoresand speculatores.[4] Indeed, communicating in cipher would have been especially important for Caesar’s exploratores and speculatoressince it was their task to find out everything about the enemy’s strengths and whereabouts and communicate this highly sensitive information back to the central command – all without the enemy knowing about this. Such exploratores and speculatoresoften came up close to the enemy’s camp, which made them vulnerable to being captured by the enemy. In fact, Caesar tells us that the Gauls sometimes captured his messengers (Caesar, The Gallic War, 5.45-46) and intercepted at least one letter sent from Caesar’s general Quintus Cicero to Caesar (5.39). If exploratores and speculatoreswere captured with letters to or from Caesar written in plaintext, then the enemy could easily have found out what was known about their forces (see for references to exploratores in Caesar’s workThe Gallic War, 1.7; 1.10; 1.12; 1.19; 1.21; 1.22; 2.5; 2.11; 2.17; 3.2; 7.11; 7.44; The Civil War, 1.62; 3.67; The African War, 12; The Spanish War, 28; see for references to speculatores in Caesar’s work The Gallic War, 2.11; 5.49). Therefore, it is likely that Caesar’s exploratores and speculatores would have used the Caesar cipher when communicating with Caesar and his generals, and amongst each other.
Although Caesar never directly discusses the use of the Caesar cipher in his works, we can find dozens of references to the sending and receiving of important confidential despatches in his works. There are 19 references in total in Caesar’s works to the sending of important confidential despatches from Caesar to his staff;[5] while Caesar’s staff sent 40 highly confidential reports back to him about the enemy’s strengths and whereabouts.[6] In addition to this, Caesar mentions 69 times that he sent word to some of his troops in general, or to specific people, without explicitly mentioning that he sent them a written message.[7] Then there are another 67 potential references to secret letters, which are situations in which Caesar left some of his forces at a certain location, and then moved on to another place with only a small part of the forces joining him.[8] And, finally there are 140 situations in which Caesar sent troops away from him or urged them to join him again.[9] This brings the total number of potential references and allusions to secret messages sent to Caesar to 128, and another 207 passages in which secret messages could have been sent. Suetonius and Cassius Dio, therefore, seem to make a reasonable argument in saying that Caesar wrote in cipher whenever he had anything confidential to say (Suetonius, Life of the Caesars 1. The Deified Julius, 56.6; Cassius Dio, Roman History, 40.9.3).
Caesar’s use of the cipher has been important to him. Indeed, the use of the cipher musthave been especially important during periods of conflict – such as the Gallic war, and even more important during the civil war in which Romans fought against other Romans.[10]In one passage (Caesar, The Gallic War, 5.48) we read that Caesar’s general Quintus Cicero (a younger brother of the orator Cicero) was besieged by the Gauls. According to Caesar’s own account, in order to let Quintus Cicero know that Caesar was about to send help, he decided to write Cicero a letter written in ‘Greek letters’ to prevent the Gauls from understanding the letter in case it was intercepted (5.48). This letter Caesar had delivered by a Gaul who worked for him (5.48). Cassius Dio presumes that Caesar simply wrote a letter in Greek to make sure that the Gauls could not understand the message (Roman History, 40.9.3-4). Cary and Foster also seem to adopt this idea in their translation of Roman History since they translate the text simply as ‘(Caesar) wrote…in Greek’ without adding any critical notes to the text and/or referring to the Caesar cipher.[11] Adams and Harris too assume that Caesar must simply have written the letter in the Greek language, without using any codes.[12]
However, a letter simply written in Greek in order to encrypt Caesar’s message seems an inadequate interpretation of the situation in this case. Correspondence between elite Romans in this period would typically have been written in Greek as a matter of course, and Caesar knew that some of the Gauls had knowledge of the Greek language and script (The Gallic War, 1.19.1; 6.14). Modern historians of cryptography Pieprzyk, Hardjono and Sebbery, therefore, seem to be in error when presuming that Caesar’s letters, if written in Greek, would have been undecipherable to his enemies in Gaul.[13] So, it seems implausible that Caesar simply wrote the letter in Greek to prevent the Gauls from comprehending its contents. Singh, Bauer, and Holmes assume that Caesar transliterated a message that was originally written in Latin, into Greek characters or letters. In this way a ‘Greek’ meaningless message was created.[14] This is plausible – in fact, the use of different languages with different alphabets (Latin and Greek) would have made the messages even more secure.
However, it must be kept in mind that the typical medium of communication amongst the Roman elite was predominantly Greek in any case. Caesar would in all probability already have communicated with Quintus Cicero using ‘Greek letters’ in his non-secret correspondence, and he would have changed to communication in cipher if an extra layer of security were needed. Moreover, since the two men would normally communicate in Greek, and Cicero was besieged by the Gauls, Caesar could not (easily) have communicated to him that he had decided to change his method of secret communication by sending a message in Latin (in a Greek alphabet), instead of in Greek. In other words, Caesar’s secret letter to Cicero was most likely a letter already written in Greek and encrypted in a Greek substitution cipher. It seems plausible then that the language for this secret communication was not simply Greek, nor Latin with a Greek substitution cipher, but, as Reinke describes it, ‘cryptic Greek.’[15] That is, a coded letter written with a Caesar cipher using the Greek alphabet. Such an interpretation is also supported by Edwards’ translation of The Gallic War in which he aptly translates ‘Graecis litteris’ as ‘Greek characters’ instead of ‘Greek letters’.[16]
We can decode this story as a veiled account of Caesar’s own cipher being used in the field as suggested by Harris.[17] We can, therefore, gain fresh insights into the cryptographic principles on which the Caesar cipher operated. In case of Caesar’s secret letter to Cicero the ‘cryptic Greek’ appears when the normal non-encrypted text is turned into encrypted text by changing every letter into the ‘character’ that could be found three places down the alphabet.
In modern cryptography, the Caesar cipher is still regarded as a simple substitution technique for encryption whereby each letter of a plaintext is replaced by a letter taken from a fixed number of positions down the alphabet.[18] Caesar most likely always used a right shift of three in the ciphertext alphabet used for encryption and decryption of his confidential correspondence – something known as monoalphabetic encryption in modern cryptography since only one ciphertext alphabet is used to encrypt and decrypt the entire message (Aulus Gellius, Attic Nights, 17.9.2-5; Cassius Dio, Roman History, 40.9.4; Suetonius, Lives of the Caesars 1. The Deified Julius, 56.6).[19]
Modern cryptographers, however, often presume that Caesar used a variety of possible ciphertext alphabets. Van Tilborg, for example, argues that Caesar shifted the alphabet over a number of places regularly to create new ciphertext alphabets – while Kahn and Oriyano presume that Caesar used up to two dozen ciphertext alphabets.[20] Although it might have been the case, theoretically speaking, that Caesar changed his shift regularly – which would have given him 23 possible ciphertext alphabets since he used the 24-letter ancient Greek alphabet – it is highly unlikely that Caesar used more than one shift of letters or changed the shift regularly since he would not have had the time nor the means to inform all of his units about this change of shift – especially not whilst on campaign. Rather, it is known from Suetonius and Cassius Dio that Caesar – whenever using the technique to create a ciphertext alphabet – substituted every alphabetic letter of a plaintext for the alphabet letter that could be found three places further down the alphabet (moving from the left to the right) with ‘A’ becoming ‘D’, ‘B’ becoming ‘E’ and so on with the rest. The Latin text in Suetonius’ work reads
quae si qui investigare et persequi velit, quartam elementorum litteram, id est D pro A et perinde reliquas commutet (Lives of the Caesars 1. The Deified Julius, 56.6)
Rolfe translates this as:
‘If anyone wishes to decipher these, and get at their meaning, he must substitute the fourth letter of the alphabet, namely D, for A, and so with the others.’[21]
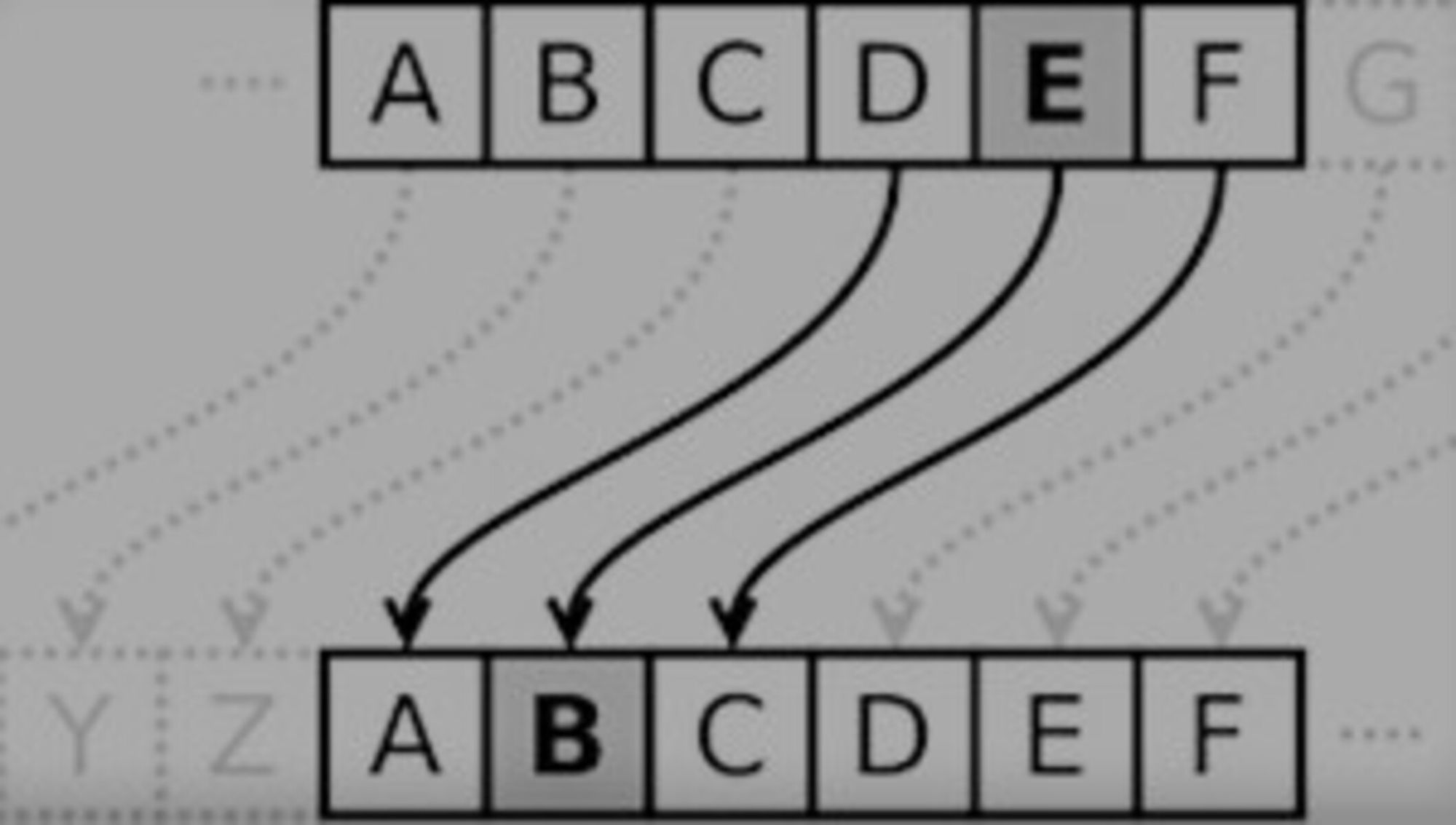
Decryption of messages written in a Caesar cipher with a right shift of three obviously worked the other way around by substituting each letter in the ciphertext for the letter that could be found three places back to the left in the alphabet (Suetonius, Lives of the Caesars 1. The Deified Julius, 56.6-7; Cassius Dio, Roman History, 40.9.3).[22]
Rolfe in his translation of Suetonius’ work, and Cary and Foster in their translation of Dio’s work, each use the word ‘substitute’ to describe these operations in their respective translations.[23] Yet in Suetonius’ work we find the word ‘commutet’, literally ‘change’; ‘alter’; or ‘substitute’, while in Dio’s work we see the word ἀντεγγράφειν (antengraphein) literally ‘insert (one name instead of another; Suetonius, Lives of the Caesars 1. The Deified Julius, 56.7; Cassius Dio, Roman History, 40.9.3).’ Rolfe, and Cary and Foster, in using the word ‘substitute’ in their respective translations, unequivocally align Caesar’s cipher with the simple substitution techniques used in modern Caesar ciphers. However, the system also reminds one of transposition in the technical sense, if the ciphertext alphabet and the plaintext alphabet are written out, one under the other.We can clearly see this in the diagrams below:
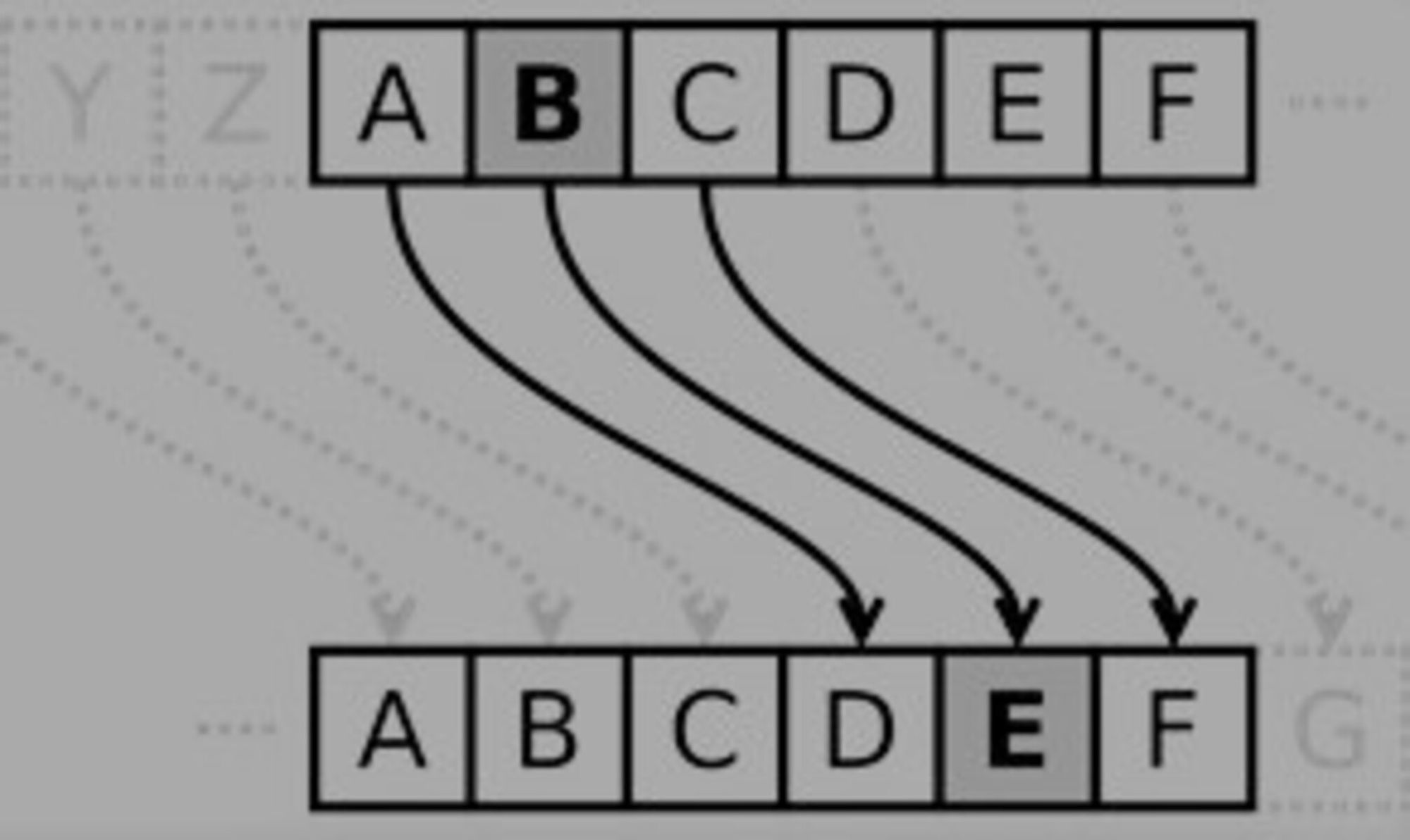
In a simple substitution cipher, the characters of a plaintext are replaced by other characters, numbers, symbols, or a combination of those – as is the case in Caesar’s substitution of plaintext letters for ciphertext letters.[24]This becomes especially clear when an encryption table is used, like the one presented in Figure 3.[25]And here, I have taken the insights from my study of Caesar’s own account of using such a shift cipher for encrypted secret communication to further suggest that the alphabet used for this shift – at least in the one case we can reasonably attribute to Caesar himself (The Gallic War, 5.48) – was not Latin but Greek (see Figure 3).
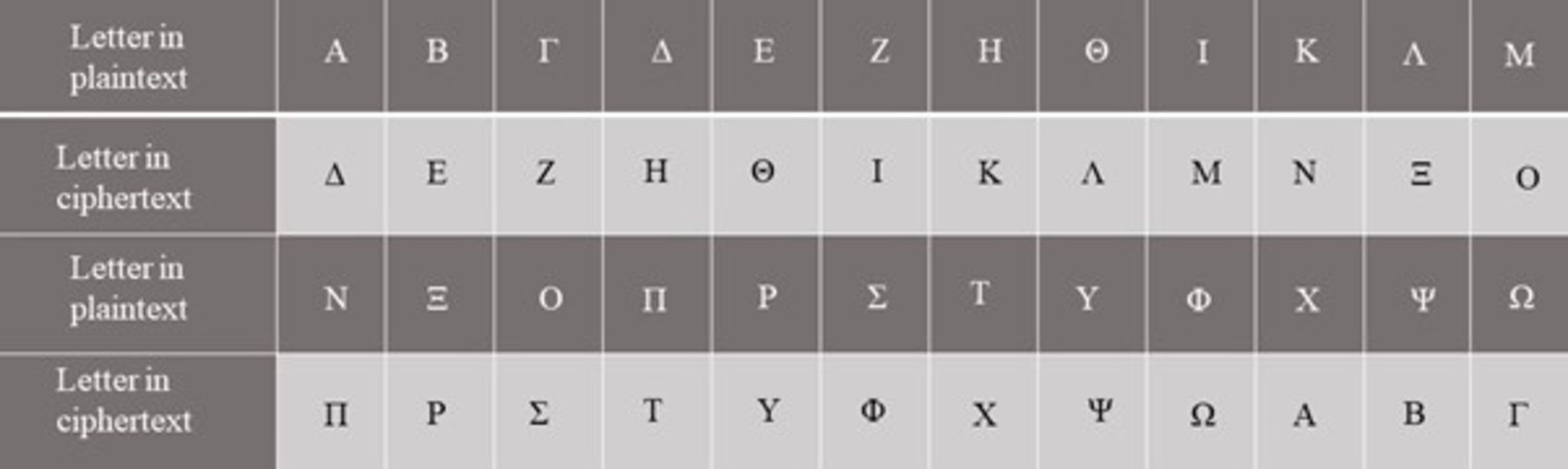
The Caesar cipher is still mentioned in almost every book on 21st-century cryptography where it is typically described as being a conceptual milestone in the development of modern cryptography.[26] Yet, none of these studies consider the significance (indirect or otherwise) of earlier Greek substitution and/or transposition ciphers including theoretical system of the Spartan scytale (see episode + article 4) upon the development and deployment of the Caesar cipher.[27]
Such modern studies typically position Caesar’s Roman technique for secret communication as the embryonic form of modern cryptographic methods and ignore the fact that complex modes of encryption already existed in the classical world and were in use centuries before the Caesar cipher. It is impossible to trace a continuous line of evolution – or, indeed, any direct relationship – between the Spartan scytale and the development of the Caesar cipher. However, the system of the Caesar cipher nevertheless shares important conceptual principles with the encryption technique utilised in the Spartan system of the scytale, known form Plutarch and Aulus Gellius (Plutarch, Life of Lysander, 19.5-7; Aulus Gellius, Attic Nights, 17.9.12-13).
When messages were unwrapped from the scytale the alphabetic letters physically changed place according to a variable ‘shift’ determined by the diameter of the scytalerod used, and in the alphabet(s) used for the encryption of the Caesar cipher we see a cipher with a right shift of three.[28] Although this later Roman cipher is less sophisticated (involving a regular, fixed, shift and not requiring any specialist equipment to supply its ‘key’) understanding the dynamics of its operation can help us to better appreciate the comparative complexity and security of the Spartan scytale system, thereby supporting the overarching argument of this book that the scytale,in theory, would have been potentially a more useful device for secret messaging than the Caesar cipher.
[1] Mollin 2005, 11; Stinson 1995, 4.
[2] See for example: Apelbaum 2007, 54; Bauer 2007, 382; Salomon 2003, 59; Salomon 2006, 243.
[3] Mollin 2005, 8; 11; Kahate 2013, 2-9; Stinson 2002, 4. See for earlier substitution ciphers: Strasser 2007, 278 (on the Atbash cipher used by Hebrew scholars ca. 600-500 BCE); Aeneas Tacticus’ How to Survive Under Siege, 31.30-31 (on replacing vowels by dots or other symbols, ca. 350 BCE).
[4] The exact difference between the two groups is uncertain. Sheldon simply presumes that speculatores were used both a spies and as scouts (Sheldon 2008, 13; 84) – while Ezov argues that speculatores gathered information through spying, while exploratores gathered information though patrols with much less secrecy (Ezov 1996, 93). Russell presumes that speculatores were agents who operate more covertly than exploratores (Russell 1999, 485). Speculatores may have played an integral part of Caesar’s military intelligence (Sheldon 1987, 106) – a point based on the idea that each of Caesar’s legions had 10 speculatores under the general staff (Perkins 1953, 84).
[5] Caesar, The Gallic War, 2.35; 5.11; 5.46; 5.48; 7.9; 7.49; 8.11; The Civil War, 1.1; 1.9; 1.10; 2.13; 2.37; 3.25; 3.78; The Alexandrian War, 34; 42; 51; 56; The African War, 4; 26; 32; 86.
[6] Caesar, The Gallic War, 2.1; 2.10; 3.19; 4.5; 4.19; 4.37; 5.1; 5.6-7; 5.11; 5.18; 5.25; 5.40; 5.45-46; 5.47; 5.49; 7.6-7; 7.41; 7.67; 7.86; 8.1; 8.4; 8.19; 8.39; 8.46; The Civil War, 1.7; 1.10; 1.18; 1.26; 1.39; 1.59; 3.18; 3.43; 3.106; Caesar, The African War, 1; 7; 31; 63; 65; The Spanish War, 18-19.
[7] Caesar, The Gallic War, 2.35; 4.38; 5.11; 5.46; 5.48; 7.9; 7.13; 7.49; 7.90; 8.11; The Civil War, 1.1; 1.9; 1.10; 2.13; 2.37; 3.25; 3.78; The Alexandrian War, 34; 42; 51; 56; The African War, 4; 26; 32; 86. For references to messages sent to specific people see Caesar, The Gallic War, 3.3; 3.19; 4.23; 4.25-26; 4.37; 5.1; 5.7; 5.52; 6.1; 7.49; 7.65; 8.27; Caesar, The Civil War, 1.8; 1.23; 1.25; 1.28; 1.82; 2.37; 3.2; 3.46; 3.62; 3.76; 3.78; 3.106-107; The Alexandrian War, 1; 9; 13; 51; The African War, 8; 12; 26; 31-32; 37; 40.
[8] Caesar, The Gallic War, 1.10; 1.15; 1.24; 2.25; 2.35; 3.7; 3.10-11; 3.28; 4.7; 4.14; 4.18-19; 4.34; 4.38; 5.1-2; 5.8; 6.3; 6.5; 6.9; 6.32-33; 6.44; 7.9; 7.11; 7.40; 7.68; 7.80; 8.2; 8.38-39; 8.46; The Civil War, 1.8; 1.15; 1.32; 1.41; 1.64; 1.72; 1.80; 1.87; 2.1; 2.22; 3.2; 3.6; 3.16; 3.52; 3.78; 3.106; The Alexandrian War, 10; 11; 14; 33; 48; 66; 73; 78; The African War, 1; 2; 9; 63; 86; 89; 98; The Spanish War, 4; 40-42.
[9] Caesar, The Gallic War, 1.21; 1.22; 1.24; 1.54; 2.17; 2.19-22; 2.26; 2.34-35; 3.1; 3.10-11; 3.16; 3.19; 3.28; 3.29; 4.14; 4.21-22; 4.32-33; 4.36; 4.38; 5.2; 5.10; 5.15; 5.24; 5.27; 6.1; 6.3; 6.5-6.7; 6.29; 6.33; 6.40-41; 7.34; 7.37; 7.45; 7.51; 7.56; 7.80; 7.87-88; 7.90; 8.2; 8.4; 8.5-7; 8.16-17; 8.19; 8.24-25; 8.43; 8.46; 8.52; 8.54; The Civil War, 1.11-12; 1.18; 1.26; 1.30; 1.32; 1.36-37; 1.39; 1.43; 1.45; 1.63; 1.66; 1.72; 1.78; 1.87; 2.5; 2.19; 2.21; 2.23; 3.8; 3.19; 3.24; 3.26; 3.34; 3.42; 3.56-57; 3.62; 3.77-78; 3.89; 3.97; 3.101; The Alexandrian War, 1; 9; 15; 17; 20; 21; 30; 31; 42; The African War, 2; 8; 10; 17-18; 20; 31; 37; 43; 51; 54; 58; 60-62; 66; 77-78; 81; 86; The Spanish War, 4; 26; 35; 39.
[10] For references to letters sent during the civil war and situations in which secret letters could have been sent see Caesar, The Civil War, 1.1; 1.7; 1.8; 1.9; 1.10; 1.11-12; 1.15; 1.18; 1.23; 1.25; 1.26; 1.28; 1.30; 1.32; 1.36-37; 1.39; 1.41; 1.43; 1.45;1.59; 1.63; 1.64; 1.66; 1.72; 1.78; 1.80; 1.82; 1.87; 2.1; 2.5; 2.13; 2.19; 2.21; 2.22; 2.23; 2.37; 3.2; 3.6; 3.8; 3.16; 3.18; 3.19; 3.24; 3.25; 3.26; 3.34; 3.43; 3.43; 3.46; 3.52; 3.56-57; 3.62; 3.76; 3.77-78; 3.89; 3.97; 3.101; 3.106-107.
[11] Cary & Foster 1914, 419.
[12] Adams 2003, 329; Harris 1989, 182-183.
[13] Pieprzyk, Hardjono & Sebbery 2013, 6.
[14] Bauer 2017, 99; 148; Holmes 1911, 218-219; Singh 1999, 10. See for similar examples of Greek texts written phonetically with the Latin alphabet and Latin texts written phonetically with the Greek alphabet e.g., P. Oxy.2.244; 36.2772; Adams 2003; Burrell 2009, 69-95; Dirkzwager 1976; Kajanto 1980; Kramer 1983; Lietzmann 1968; Rea 1968; 1970; Wouters 1976.
[15] Reinke 1962, 114.
[16] Edwards 1917, 297.
[17] Harris 1995, 14.
[18] Mollin 2005, 11; Stinson 1995, 4.
[19] Apelbaum 2007, 54; Bauer 2007, 382; Salomon 2003, 59; Salomon 2006, 243.
[20] Kahn 1974, 77; Oriyano 2013, 56; Van Tilborg 2006, 9.
[21] Rolfe 1914, 109.
[22] See also Figure 1 for encryption with the Caesar cipher, and Figure 2 for decryption with the Caesar cipher.
[23] Cary & Foster 1914, 419; Rolfe 1914, 109.
[24] If using the Classical Latin alphabet for his cipher, Caesar had an alphabet of either 21 or 23 letters. According to Cicero, the alphabet of the late Republican period was composed of 21 letters (On the Nature of the Gods, 2.37): the letters ‘J’, ‘U’, ‘W’, ‘Y’ and ‘Z’ were not used – although according to Sherwood, Nikolic, et al., the Romans already added the Greek letters ‘Y’ and ‘Z’ to their alphabet after the conquest of Greece in 146 BCE (Sherwood, Nikolic et al. 2003, 525; see also Wallace 2015, 14; 16).
[25] See for example: Bauer 2013; Churchhouse 2002; Piper & Murphy 2002; Purnamaa & Rohayani 2015; Van Tilborg 2006, 9-10.
[26] Stewart, Chapple et al. 2012, 362. See also Kahn 1967, 77; Mollin 2005, 11; Oriyano 2013, 56; Stinson 2002.
[27] There is an ongoing debate on whether Caesar wrote his secret messages (including the message to Cicero) (1) fully in Greek (using Greek characters, accidence, and syntax), (2) in Latin with a Greek substitution cipher, or (3) in Greek with a Greek substitution cipher. Therefore, there are numerous ways in which Greek cryptographic methods may have influenced later Roman cryptographic methods. In this case, I assume that Caesar’s secret letters were written in Greek with a Greek substitution cipher.
[28] Augustus used the same principle as Caesar, yet with a right shift of one hereby writing B for A, C for B, et cetera (Suetonius, Lives of the Caesars 2. The Deified Augustus, 88). This right shift of one can again be seen in Viking texts (Bauer 2017, 118-120), and in the work of the 14th century CE Greek scholar Georgius Chrysocossas who used β for α, γfor β and so on. A partial Latin translation of the work of Georgius Chrysocossas can be found in various 15th- and 16th-century copies of a manuscript known as Expositio In Syntaxin Persarum (Gardthausen 1911, 302).
Bibliography:
Adams, J. N. (2003). Bilingualism and the Latin Language. Cambridge: Cambridge University Press.
Apelbaum, Y. (2007). User Authentication Principles, Theory and Practice. Second Edition. Pewaukee: Fuji Technology Press.
Bauer, C. P. (2013). Secret History: The Story of Cryptology. Boca Raton/ London/ New York: CRC Press - An Imprint of Taylor and Francis Group.
Bauer, C. P. (2017). Unsolved! The History and Mystery of the World's Greatest Ciphers from Ancient Egypt to Online Secret Societies. New Jersey/ Woodstock: Princeton University Press.
Bauer, F. L. (2007). Decrypted Secrets: Methods and Maxims of Cryptology. Berlin/ Heidelberg/ New York: Springer-Verlag.
Burrell, B. (2009). Reading, Hearing, and Looking at Ephesos. In Johnson, W. & Parker, H. Ancient Literacies: The Culture of Reading in Greece and Rome. Oxford: Oxford University Press, 69-95.
Cary, E., & Foster, B. (1914). Dio Cassius: Roman History (Volume III: Books 36-40; Loeb Classical Library 53). Cambridge (Massachusetts): Harvard University Press.
Chesire Library Science (2013). Caesar Cipher Encryption and Decryption tables. Retrieved from: http://chesirelibraryscience.files.wordpress.com/2013/03/caesa_cipher_left_ shift_of_3-svg.com
Churchhouse, R. F. (2002). Codes and Cipher: Julius Caesar, the Enigma and the Internet. Cambridge: Cambridge University Press.
Dirkzwager, A. (1976). Latijns Grieks. Hermeneus Tijdschrift voor Antieke Cultuur, 48 (2), 125-129.
Edwards, H. J. (1917). Caesar: The Gallic War (Volume 72 Loeb Classical Library). Cambridge (Massachusetts): Harvard University Press.
Ezov, A. (1996). The "Missing Dimension" of C. Julius Caesar. Historia: Zeitschrift für Alte Geschichte, 45 (1), 64-94.
Gardthausen, V. E. (1911). Griechische Paleographie (Volume 2: Die Schrift, Unterschriften und Chronologie im Altertum und im Byzantinischen Mittelalter). Leipzig: Veit & Comp.
Harris, R. (1995). Enigma. London: Arrow Books.
Harris, W. V. (1989). Ancient Literacy. Cambridge (Massachusetts): Harvard University Press.
Holmes, T. R. (1911). Caesar's Conquest of Gaul(2nd edition: revised throughout and largely rewritten ed.). Oxford: Clarendon Press.
Kahate, A. (2013). Cryptography and Network Security. Porur (Chennai): McGraw Hill Education.
Kahn, D. (1967). The Codebreakers: The Comprehensive History of Secret Communication from Ancient Times to the Internet. London: Weidenfeld and Nicolson.
Kahn, D. (1974). The Codebreakers: The Comprehensive History of Secret Communication from Ancient Times to the Internet (2nd edition, abridged). London: Weidenfeld and Nicolson.
Kajanto, I. (1980). Minderheiten und ihre Sprachen in der Hauptstadt Rom. In: Neumann, G. & Untermann J., (eds.), Die Sprachen im Römischen Reich der Kaizerzeit: Kolloquium vom 8. bis 10. April 1974. Cologne: Rheinland, 83-101.
Kramer, J. (1983). Glossaria Bilinguia in Papyris et Membranis Reperta. Bonn: Habelt.
Lietzmann, H. (1968). Kleine Texte für Vorlesungen und Übungen, 17-18. Begründet von Hans Lietzmann. Herausgegeben von Kurt Aland. Berlin: Verlag Walter de Gruyter & Co.
Mollin, R. A. (2005). Codes: The Guide to Secrecy From Ancient to Modern Times. Boca Raton/ London/ New York/ Singapore: Chapman & Hall/CRC - An imprint of Taylor and Francis Group.
Oriyano, S.-P. (2013). Cryptography InfoSec Pro Guide.New York/ Chicago/ San Francisco/ Athens/ London/ Madrid/ Mexico City/ Milan/ New Delhi/ Singapore/ Sydney/ Toronto: McGraw Hill Education.
Perkins, E. J. (1953). The Military Staff – Its History and Development. Military Review, 33 (6), 81-88.
Pieprzyk, J., Hardjono, T., & Seberry, J. (2013). Fundamentals of Computer Security. Berlin: Springer Science & Business Media.
Piper, F., & Murphy, S. (2002). Cryptography: A Very Short Introduction. Oxford: Oxford University Press.
Purnamaa, B., & Rohayani, A. H. (2015). A New Modified Caesar Cipher Cryptography Method With Legible. Procedia Computer Science,59, 195–204.
Rea, J. (1968). Oxyrhynchus Papyri 2660/2660(a). In: Parsons, P., Rea, J. & Turner, E. (eds.), The Oxyrhunchus Papyri (Volume XXXIII). London: The Egypt Exploration Society, 77-79.
Rea, J. (1970). Oxyrhynchus Papyri 2772: Instructions to a Banker. In: Coles, R., Foraboschi, D., Soliman El-Mossalamy, A., Rea, J. & Schlag, U. (eds.), The Oxyrhynchus Papyri (Volume XXXVI). London: The Egypt Exploration Society, 63-65.
Reinke, E. C. (1962). Classical Cryptography. The Classical Journal, 58 (3), 113-121.
Rolfe, J. C. (1914). Suetonius: Lives of the Caesars(Volume 31; Loeb Classical Library: I: Julius. Augustus. Tiberius. Gaius. Caligula). Cambridge (Massachusetts): Harvard University Press.
Russell, F. S. (1999). Information Gathering in Classical Greece. Ann Arbor: University of Michigan Press.
Salomon, D. (2003). Data Privacy and Security: Encryption and Information Hiding. New York: Springer.
Salomon, D. (2006). Coding for Data and Computer Communications. New York: Springer.
Sheldon, R. M. (1987). Tinker, Tailor, Caesar, Spy: Espionage in Ancient Rome. Ann Arbor: UMI Dissertation Information Service.
Sheldon, R. M. (2008). Espionage in the Ancient World: An Annotated Bibliography of Books and Articles in Western Languages. Jefferson/ London: McFarland and Company Incorporated Publishers.
Sherwood, A. N., Nikolic, M., Humphrey, J. W., & Oleson, J. P. (2003). Greek and Roman Technology: A Sourcebook: Annotated Translations of Greek and Latin Texts and Documents. London/ New York: Routledge - An Imprint of Taylor and Francis Group.
Singh, S. (1999). The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography. London: Fourth Estate.
Stewart, J., Chapple, M., & Gibson, D. (2012). CISSP: Certified Information Systems Security Professional Study Guide. Hoboken: John Wiley and Sons Incorporation.
Stinson, D. R. (1995). Cryptography: theory and practice. Boca Raton/ New York/ Washington D.C.: CRC Press.
Stinson, D. R. (2002). Cryptography: Theory and Practice. Second edition. Boca Raton/ London/ New York/ Washington D.C.: Chapman and Hall - An imprint of CRC Press Company.
Strasser, G. F. (2007). The Rise of Cryptology in the European Renaissance. In: De Leeuw, K. & Bergstra, J. A. (eds.), The History of Information Security: A Comprehensive Handbook. Amsterdam/ Boston/ Heidelberg/ London/ New York/ Oxford/ Paris/ San Diego/ San Francisco/ Singapore/ Sydney/ Tokyo: Elsevier, 277-325.
Van Tilborg, H. C. (2006). Fundamentals of Cryptology: A Professional Reference and Interactive Tutorial by Henk C. A. van Tilborg, Eindhoven University of Technology, The Netherlands (second edition). Boston/ Dordrecht/ London: Kluwer Academic Publishers.
Wouters, A. (1976). “Latijns Grieks” en “Grieks Latijn”, over Translitteraties en hun Bedoeling. Hermeneus Tijdschrift voor Antieke Cultuur, 48 (4), 179-191.






